The mystery "Deloitte"-blog
While seaching the web for information on a camera I have ordered, I stumbled upon a suspicious site hosted on deloitte.com. It turned out the be a malicious site. This is the story of how it was taken down, and the path to writing about it.

I recently ordered a new camera that I have been eagerly awaiting to have delivered. I later found out that this is the favorite camera of the internet - the Fujifilm X100VI. Naturally, I started searching for information on delivery times, but without luck. I did however stumble upon a weird site:
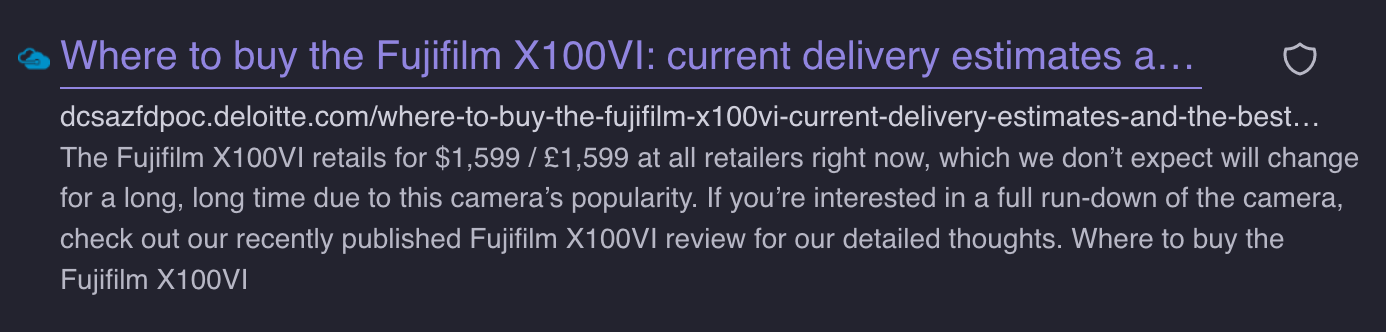
What on earth is dcsazfdpoc.deloitte.com? Is this actually Deloitte, as in one of the largest companies on the planet? Why would they be writing about when I could get my camera? Hoping that I might have struck gold, and found a secretive blog that might hold some answers, i clicked the link.
The article is everything one might expect. It describes the pain of waiting for a great camera, has some vague tips on how you might get ahead of the queue, and lists some alternatives if you need a camera in you hands right now. Unfortunately for me, there are no big insights, and no exclusive shortcuts to faster delivery.
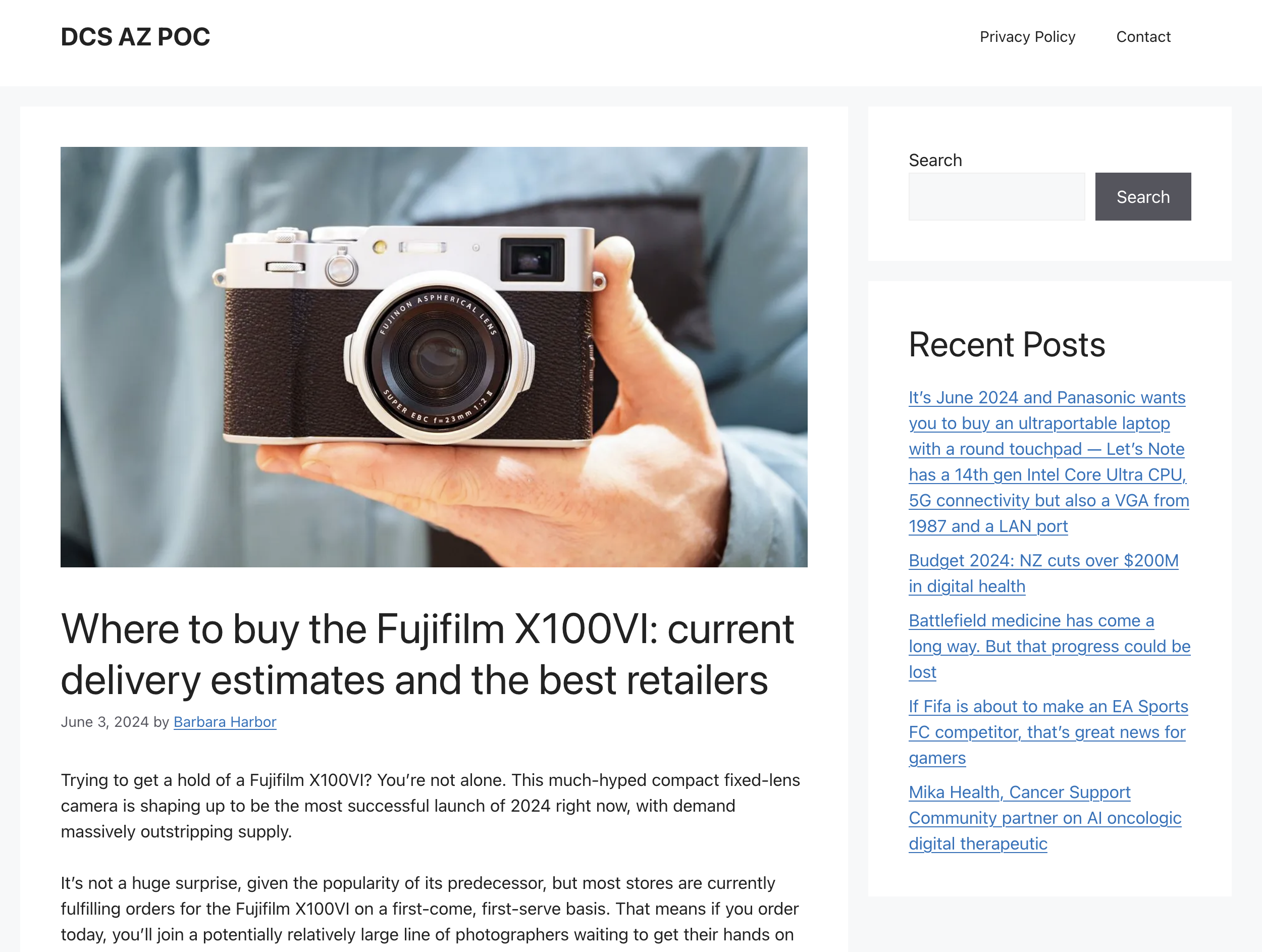
But there are a few interesting things. Most of the images in the article wasn't loading properly, the site looked quite unfinished, but most importantly, at the bottom of the article is a link to a source. A TechRadar article that is word for word identical to the "Deloitte article". What on earth is going on here?
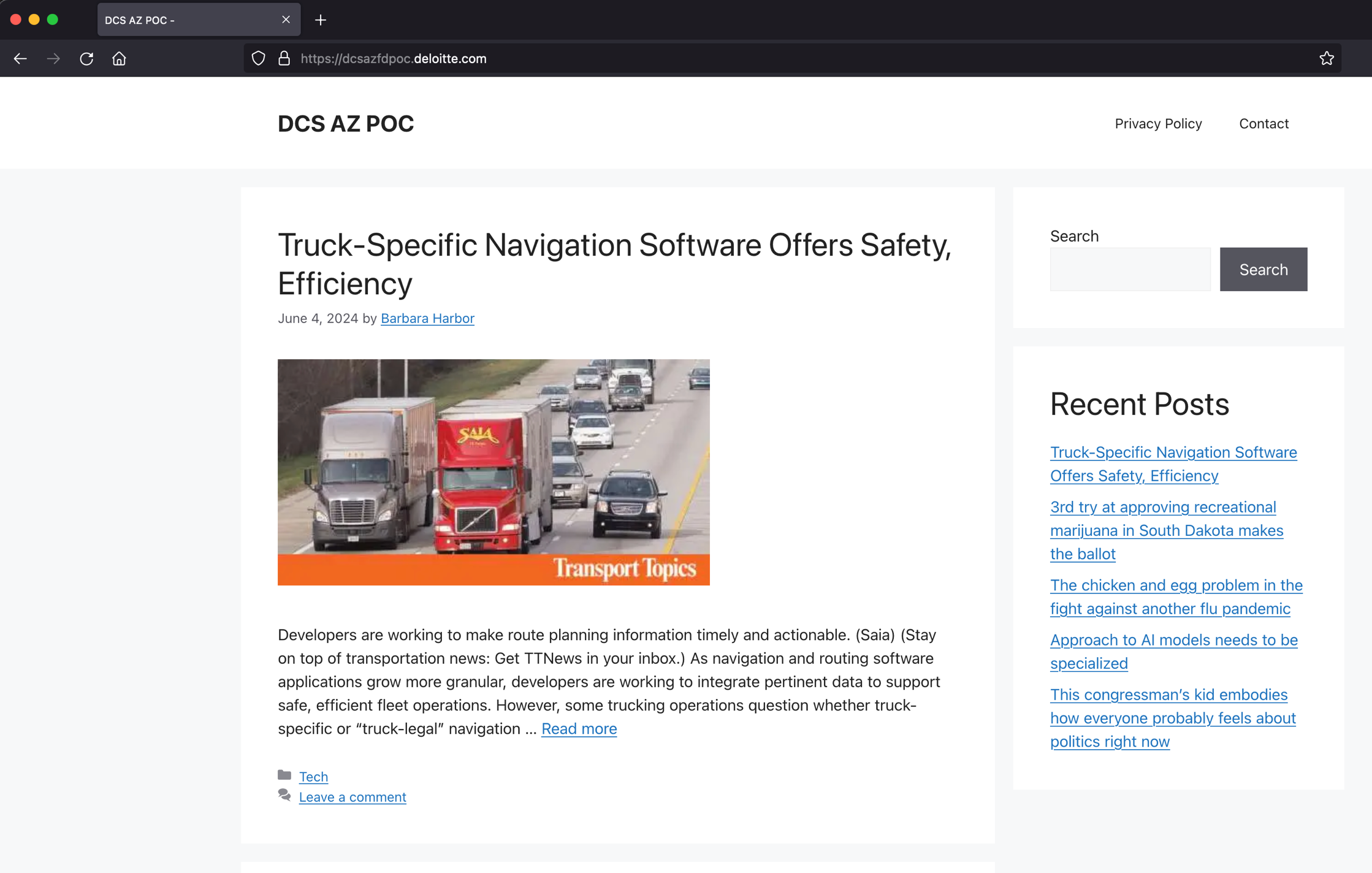
Going to the front page of what we will call "the mystery site" shows us a blog style website with various articles. And I mean various - there seems to be no common theme, there are articles on my camera, on shutting pharmacies in the US, navigation systems for trucks, the interest rate in Canada, a vote about legalizing marijuana in South Dakota.
And there are a lot of posts! It fills more than 400 pages! And they keep coming at an alarming rate. A couple of new articles actually popped up in the hour after I started looking at the site.
While all articles on the site have an author connected to them, this is never the name we find if we follow the source link in the article.
It appears that the mystery site has fictional authors that claim credit for these articles.
The contact information on the site is of course not helpful:
Doing more searches on the title of the page - "dcsazfdpoc" - only deepens the mystery. I find a GitHub-repo that appears connected to the site, but it returns 404.

The GitHub-user also appears to be gone, but searching for it gives a few more hits:
I'm starting to get a bad feeling. Is this a person that has been trying to create fake sites for known domains? I try to access the URLs, and a couple are taken down, a couple are not.
But they seem to have one thing in common. They are all hosted on azure. Looking at the URL for the mystery site, I think we can decode it as follows:
DCS: Deloitte Solutions Center (yes, that is an abbreviation they use for that)
AZ: Azure
FD: Front door (an Azure product)
POC: Proof of concept
Time to make some calls!
At this point I am certain that this is not a real site that Deloitte would have published. My goal shift from learning more about the site, to finding the fastest way to get the right people's attention, and having it taken down.
Unfortunately, Deloitte does not maintain a security.txt-file on their site. I was also unable to find contact information aimed at security researchers, or a global or local Security Operations Center (SOC). I reached out to my network to see if anyone had a point of contact. Some people knew employees in other departments, but I worried I would be thrown around in the organization if I did not get to speak to someone with an understanding of IT security. I did some research, and ended up cold calling one of the partners in the cyber security department, crossing my fingers that I wouldn't be immediately hung up on.
I have to say that the experience turned out great. I was taken seriously from the start, and quickly led to the correct point of contact in Deliotte Norway. Within a couple of hours of my email to the point of contact, Deloitte confirmed my finding, and engaged their SOC. For a large corporation like this to be able and willing to turn around quickly based on the findings of someone they have never heard of is impressive.
A couple of days after I reached out, I could confirm that the site was no longer reachable. A job well done, and a well deserved pat on the back for me.
Thank you - but please don't mention us
A couple of weeks after the site was taken down, I received an email from my point of contact in Deloitte Norway. He confirmed that a subdomain had been compromised, and that the site had been taken down and control over the domain was once again in Deloitte's hands.
It's unfortunately at this point Deloitte's response to the issue fell short of being perfect. I had mentioned that I was going to publish about the finding when the site had been taken down. I did this so Deloitte could coordinate with me in case they had any remaining fixes that needed to go out before the issue was published. However, at this point Deloitte informs me that they don't want me to mention their company by name if I decide to write about the incident.
I was both disappointed, discouraged and a bit frightened by this response. Deloitte runs a large cyber security division. I would expect them to understand the need for security researchers to be able to talk openly about their findings (as long as this does not endanger systems), and it also left me feeling like the finding was not really appreciated by Deloitte. How important can something be when you just sweep it under the rug?
The sensation of fear comes from the history a lot of companies have with not only ignoring or downplaying the findings of security researchers, but also choosing legal action against those why try to help them. While nothing at this point indicates Deloitte wants to go down that road, they do employ 2500 lawyers globally. So what would be the consequences of trying to stand up to them?
With the help of some colleagues, I decided to try to reason with Deloitte, and make them understand why I would need to publish the full story - including their name. I think I owe that explanation to you as a reader as well:
First of all, the story is relevant to you because I'm telling you the whole story. A story of me finding some compromised site somewhere on the internet is not very interesting, nor does it really teach you anything about the state of internet security. By telling the whole story I'm also providing the possibility of fact checking. While the site has been taken down, traces of it is still accessible in the web archive, and other services may still contain necessary information to confirm the story.
I also think that we as an industry must be open about all kinds of incidents. There are too few of the good guys, and we need all the help we can get. Reading about where others have made mistakes enables the rest of us to act proactively, and take defensive steps. When we are open about both incidents and mistakes, we support the rest of the information security community in hardening their systems.
I brought these arguments up with my contact at Deloitte, and was pleasantly surprised with the response: They understood my reasons for wanting to write about this, and no longer objected to the publication. They would however like an opportunity to review the post before publication and provide feedback, which I found understandable and reasonable.
How did this happen?
I do not have a clear idea of how this site came to be. In my mind there are two theories that are more likely.
Either there was system running at the address in question and this system was taken over. Someone could have set up a Proof of Concept for using Azure Front Door, but not secured it well enough, and this has been taken over by a threat actor. This could have happened in any number of ways, either a known vulnerability in a dependency, a leaked credential or more targeted hacking.
It's also possible that there was at some point a legit site hosted at this address, that was later removed completely. If the CNAME-record verifying the domain was left intact in Deloitte's DNS, or the underlying domain that dcsazfdpoc.deloitte.com was pointing to had been re-registred by the attacker, then that could enable someone else to set up a different app at the same domain. This attack vector was covered on a recent episode on Security Now. In large organizations, keeping up with all registered DNS-records can be a daunting task, and this could lead to vulnerabilities.
Every failure is a learning opportunity!
I strongly believe that failure is nothing but an opportunity for learning. In this case the consequences of the failure was mild, but the learning has been great - at least for me.
I have learned that you can pick up the phone and alert a giant international corporation about a security problem, and have them take swift action to fix the issue. I have also learned that it is worthwhile to have a respectful discussion about disclosure, and that this industry is filled with a lot of pragmatic people (perhaps contrary to popular belief).
I have also learned that writing a blog post about such a case is a lot of work, and easily finds its way to the bottom of the pile in the hustle and bustle of life. I'm very impressed with the people in the security industry who seem able to churn out stuff like this on a weekly basis.
Timeline
2024-06-03 - I stumble upon the "Deloitte-blog".
2024-06-03 - I start reaching out to my network to get a point of contact at Deloitte.
2024-06-04 - I establish contact with Deloitte Norway.
2024-06-04 - Deloitte Norway acknowledges the issue and engages their SOC.
2024-06-06 - I confirm on my end that the site was taken down.
2024-06-21 - Deloitte confirms the site is taken down, and requests that I do not publish the involvement of Deloitte. I take some time to discuss this with colleagues and to assess the risk of going against this request.
2024-07-06 — I inform Deloitte that I will be publishing the finding and will not omit their company name. I ask them to reevaluate their stance.
2024-08-12 – Deloitte informs me that they will not object to publication, but would like a preview of the blog.
2024-10-28 – A draft of this post is sent to Deloitte.
2024-11-02 – Deloitte informs me that the blog post is factually correct, and that they have nothing further to add.
